What is structure of JWT token
In our previous post we explained about how JWT is used as an authorization strategy for web security and why it is so popular these days. In this article we will look into the structure of JWT in detail and how its structure helps to achieve most of the utilities it provides.
JWT token looks something like below
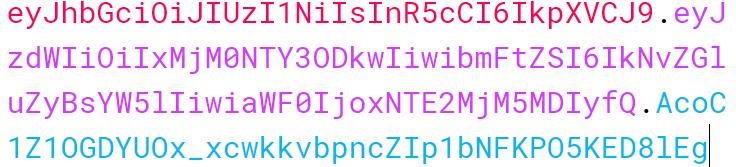
If you look closely, the token consists of three parts separated by a dot. Here each part is represented in three different colors. If you decrypt the token you will see that the three parts represent following component:
Lets look at the signature structure below
Header – First part is the header. It again consists of two elements alg and typ. Alg represents algorithm used to verify signature which is the last part and type is “JWT”. Header is base-64 encoded.
Payload – This is the main part of the whole token which contains the user information. As we know the JWT is a value token and the whole point of using JWT token is to send some value from server to client which can be used in subsequent request. In case of authorization the value is user information. Payload is again base-64 encoded. No confidential information should be added to the payload as these are public information. Any body can decrypt this encrypted payload using base-64 decoder.
Signature – This is the final part which the server uses to validate whether the token is correct or not. The server creates the signature and signs the token with this signature and send it to the client. This signature contains a secret key which only server knows. So when the client send the token back in the subsequent request, server validates the signature and if it matches the response is sent.
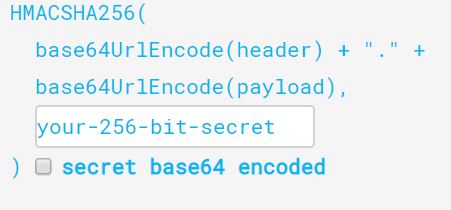
As you can see signature is created using the algorithm mentioned in header (HS256). Server creates a hashed value of combination of
(Base-64 encrypted header + Base-64 encrypted payload + secret key) and attach it as signature of the token. So if someone tampers the value in payload and send the new JWT token in subsequent request , server will reject that token as the old signature will not match with the one computed by the server for the new payload.
Also Read : JWT Token and its usage in Authorization